Problem Statement – (Securing web applications deployed on GCP with external Identity providers using SAML Integration)
External entities / clients able to use SSO based sign-in using any of the 3rd party external Identity providers (iDP) like Azure AD, Auth0 etc before they are allowed to access applications deployed on GCP.
Advanced use case could be as multi tenant setup with each tenant using a different iDP (Okta, Auth0, Azure SSO)
External Client / User —> HTTP LB with CR setup (could be any other backend like GCE or GKE) → IAP → CR (Backend)
Level Setting
SAML is a protocol that allows for secure authentication and authorization in a single sign-on environment, ensuring that users can access multiple services with a single login while maintaining security and trust between parties. Other types of authentication mechanisms are OIDC, JWT tokens etc
Understanding SAML integration and authentication flow
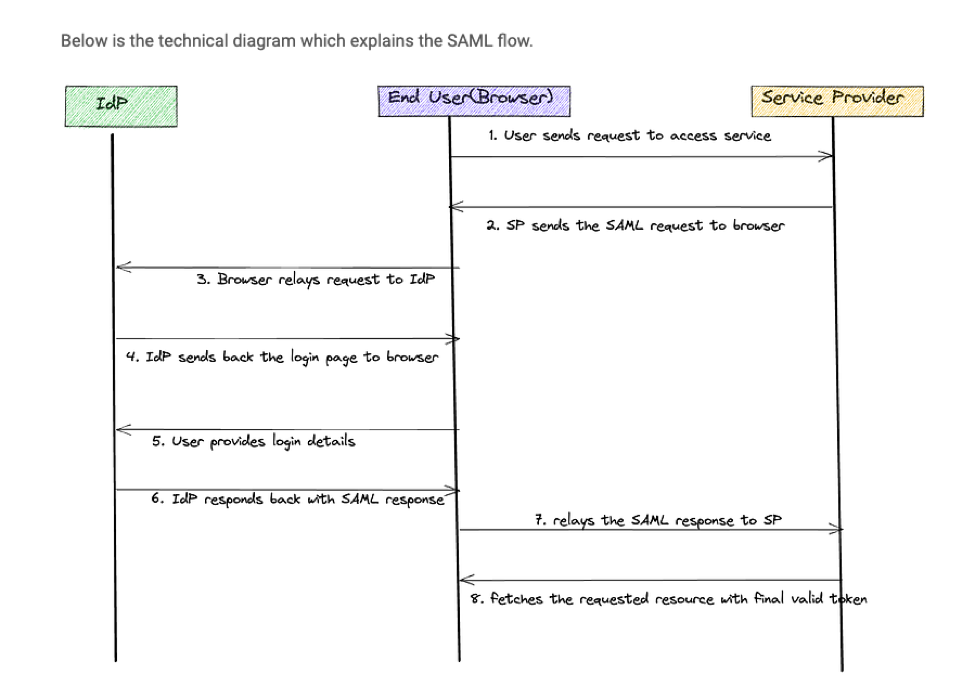
SAML, which stands for Security Assertion Markup Language, is an XML-based standard used for exchanging authentication and authorization data between parties, particularly in web-based single sign-on (SSO) systems. SAML enables secure communication between an identity provider (IdP) and a service provider (SP) to facilitate user authentication and authorization without the need for users to provide their credentials to each service individually.
Here’s a basic explanation of how SAML works with some examples:
Parties involved
Identity Provider (IdP): This is the system responsible for authenticating users and generating SAML assertions (security tokens) that contain user information. Examples are Auth0, OKTA, Azure AD etc
Service Provider (SP): This is the system or application that users want to access after authentication. (In our case it is an application deployed on GCP)
SAML integration flow
Architecture
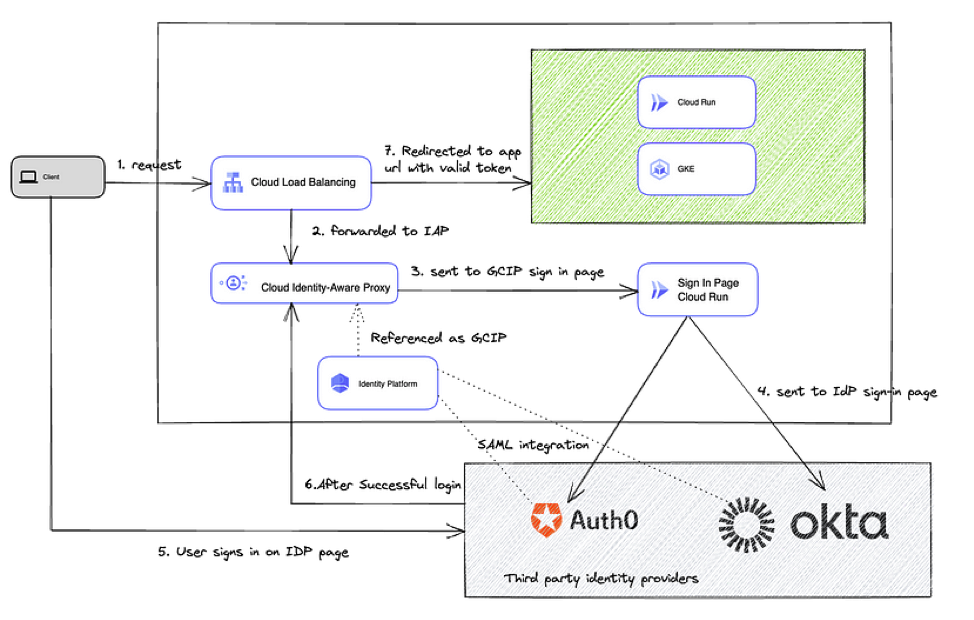
GCP Services used
- HTTP LB in front of the target application
- Cloud IAP – Identity aware proxy to restrict users to specific app domains
- Google Cloud Identity Platform (GCP service)
- External / 3rd party iDP – OKTA, Auth0 etc
- (Optional) Custom sign-in page hosted on CR OR you can use the default login page that comes with IAP to speed up SAML integration.
- Target application that will be accessed by end users (sdP) in our case this is deployed on GKE or CR (See green box above)
Steps to setup SAML integration
- Assumption is a target application is already deployed on GCP (CR, GCE or GKE). This is the application that needs to be secured by SAML integration.
- Configure iDP
- Depending on what provider you use Auth0, OKTA login to the the provider’s console and setup following
- Enable SAML web application add-on
- Get all iDP login details we need these later
- Depending on what provider you use Auth0, OKTA login to the the provider’s console and setup following
- Configure Identity Platform in GCP for each provider (as in the case of a multi tenant application with each tenant using a separate iDP)
- Choose sign-in method as SAML
- Name: Provide a relevant name
- Entity Id: Will be the issuer you get from Auth0
- SSO URL: IdP login URL (from Step 2a)
- Certificate: Put the SAML certificate
- EntityId: Provide something unique of your choice
- Configure Cloud IAP to use Identity Platform
- Open the IAP page in the Google Cloud console.
- Select the same project that you configured Identity Platform with. Using different projects is not supported.
- Select the Applications tab.
- Locate the App Engine app or Compute Engine service you want to restrict access to using IAP.
- Toggle the switch in the IAP column to On.
- In the side panel, click Start in the box labeled Use external identities for authorization.
- Confirm your selection.
- In the Identity Platform side panel: Choose whether to build your own sign-in page, or have IAP create one for you.
- Add authorized domains on the iDP side
- Go back to Identity Platform and whitelist a few domains
- Add the following domains:
- cloud-run-********************.com [Web application page URL]
- dev-**************.us.auth0.com [Auth0 URL]
- iap-gcip-hosted-ui-c***********-backend-vkffmroceq-de.a.run.app [Custom sign in page hosted on Firebase, Cloud Run, or your own URL]
- iap.googleapis.com [iap apis]
- Create users in iDP to test
- Test the Application
